
Hackers Exploit Avast Anti-Rootkit Driver to Disable Security Defenses
In a recent malicious campaign, hackers have been found exploiting an old and vulnerable Avast Anti-Rootkit driver to evade detection and take control of target systems by disabling security components. This sophisticated attack leverages a technique known as bring-your-own-vulnerable-driver (BYOVD), allowing the malware to operate at the kernel level and terminate critical security processes.
The Malware and Its Mechanism
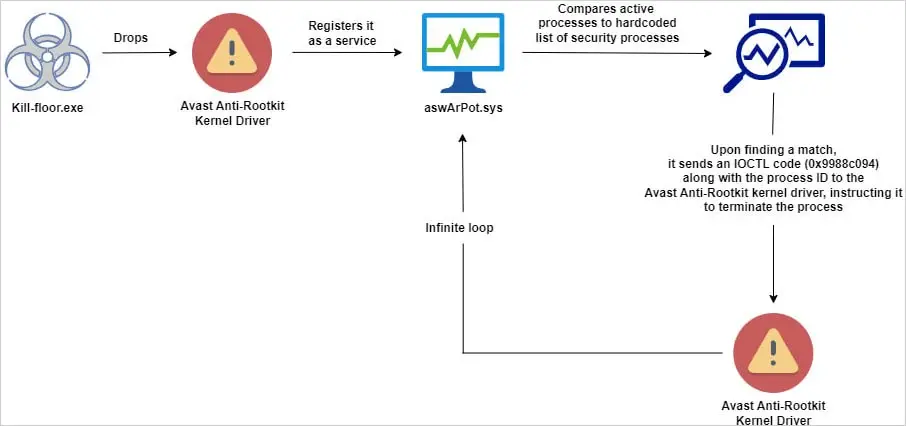
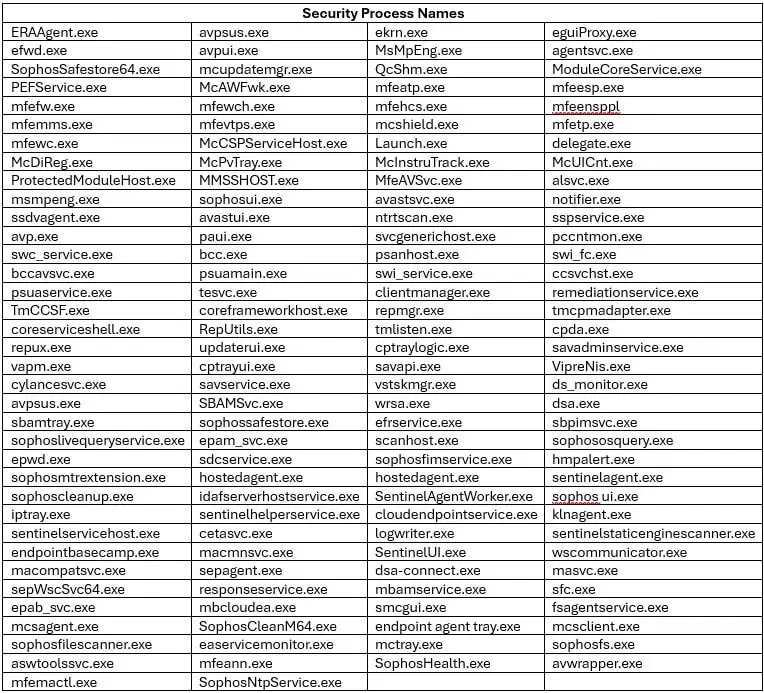
The malware responsible for this attack is a variant of an AV Killer, not belonging to any specific family. It includes a hardcoded list of 142 security process names from various vendors. By operating at the kernel level, the driver provides access to critical parts of the operating system, enabling the malware to terminate these processes.
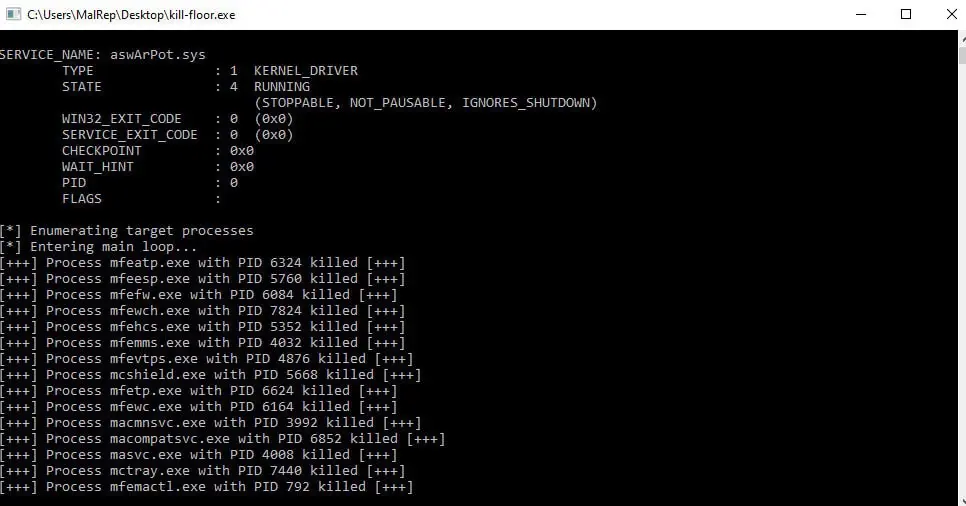
Security researchers at Trellix discovered this attack, noting that the malware, named kill-floor.exe, drops the vulnerable driver ntfs.bin into the default Windows user folder. The malware then creates a service named aswArPot.sys using the Service Control (sc.exe) and registers the driver. It uses a hardcoded list of 142 processes associated with security tools, checking them against multiple snapshots of active processes on the system. When a match is found, the malware creates a handle to reference the installed Avast driver.
Exploiting the Driver
The malware leverages the DeviceIoControl API to issue the necessary IOCTL commands to terminate the targeted processes. This method allows the malware to disable security solutions from various vendors, including McAfee, Symantec (Broadcom), Sophos, Avast, Trend Micro, Microsoft Defender, SentinelOne, ESET, and BlackBerry. With defenses deactivated, the malware can perform malicious activities without triggering alerts or being blocked.
Historical Context and Similar Attacks
This technique is not entirely new. In early 2022, researchers at Trend Micro observed similar procedures while investigating an AvosLocker ransomware attack. In December 2021, the Stroz Friedberg Incident Response Services team found that Cuba ransomware used a script to abuse a function in Avast's Anti-Rootkit kernel driver to kill security solutions on victim systems.
Around the same time, SentinelLabs researchers discovered two high-severity flaws (CVE-2022-26522 and CVE-2022-26523) in the Avast Anti-Rootkit driver, present since 2016. These vulnerabilities could be exploited to escalate privileges and disable security products. Avast addressed these issues with security updates in December 2021.
How to Stay Safe
To protect against attacks that exploit vulnerable drivers, consider the following measures:
Update Security Software Regularly: Ensure all security software and drivers are up to date with the latest patches and updates. This helps mitigate known vulnerabilities.
Implement Driver Blocklists: Use driver blocklists to prevent the installation of known vulnerable drivers. Microsoft provides a vulnerable driver blocklist policy file, which is updated with every major Windows release and is active by default on Windows 11 2022 and later versions.
Use Endpoint Detection and Response (EDR) Solutions: Deploy EDR solutions that can detect and respond to suspicious activities, including attempts to exploit vulnerable drivers.
Monitor and Audit Systems: Regularly monitor and audit systems for unusual activities or changes, such as the creation of new services or the installation of unexpected drivers.
Employ Application Control: Use application control solutions to restrict the execution of unauthorized applications and drivers. This can help prevent malware from dropping and executing vulnerable drivers.
Educate and Train Staff: Ensure that IT staff and users are aware of the risks associated with vulnerable drivers and the importance of maintaining up-to-date security measures.
How Cy-Napea® Can Help
Cy-Napea® offers a comprehensive suite of advanced cybersecurity solutions designed to protect against sophisticated threats like the one described. Here’s how Cy-Napea® can enhance your security posture:
Endpoint Detection and Response (EDR): Cy-Napea®'s EDR capabilities ensure that every endpoint is meticulously monitored and protected. This helps in detecting and responding to threats in real-time, minimizing damage and ensuring swift recovery.
Extended Detection and Response (XDR): By integrating data from multiple security layers, Cy-Napea®'s XDR provides a holistic view of threats, enabling more effective detection and response.
Managed Detection and Response (MDR): Cy-Napea®'s MDR service offers 24/7 monitoring by cybersecurity experts, ensuring that threats are identified and mitigated promptly.
Vulnerability Assessments: Regular vulnerability assessments help identify and address potential weaknesses in your systems before they can be exploited.
Centralized Management: Cy-Napea® provides centralized management of security policies and configurations, making it easier to enforce security measures across all devices.
Data Loss Prevention (DLP): Protect sensitive data from unauthorized access and exfiltration with Cy-Napea®'s DLP solutions.
By leveraging Cy-Napea®'s advanced cybersecurity solutions, organizations can significantly enhance their defenses against attacks that exploit vulnerable drivers and other sophisticated threats.
Read the original article here




