
EDRSilencer: The New Threat Targeting EDR Tools in Red-Team Operations
A new open-source tool, called EDRSilencer, has emerged as a significant threat in cybersecurity incidents, aiming to detect security tools and silence their alerts to management consoles. This alarming trend has caught the attention of security researchers, who are closely monitoring how attackers are integrating EDRSilencer into their tactics to evade detection.
Researchers at Trend Micro, a leading cybersecurity company, have identified multiple attempts by threat actors to incorporate EDRSilencer into their attacks. According to Trend Micro, this development is a concerning evolution in the tactics of cyber adversaries.
“Our internal telemetry showed threat actors attempting to integrate EDRSilencer in their attacks, repurposing it as a means of evading detection,” said Trend Micro.
What is EDRSilencer and How Does it Work?
Endpoint Detection and Response (EDR) tools are essential security solutions designed to protect devices from cyber threats. They leverage advanced analytics and constantly updated intelligence to detect both known and novel threats. EDRs not only respond automatically to these threats but also generate detailed reports that provide defenders with critical information about the origin, impact, and propagation of the threat.
EDRSilencer, an open-source tool, takes aim at these critical security defenses. It is inspired by MdSec NightHawk FireBlock, a proprietary penetration-testing tool, and is designed to detect active EDR processes. It then uses the Windows Filtering Platform (WFP) to monitor, block, or manipulate network traffic over IPv4 and IPv6 protocols.
WFP is a core component used in many security solutions, including firewalls and antivirus software. It provides a mechanism to set filtering rules that control how network traffic flows on a device. By exploiting this feature, EDRSilencer can tamper with the data exchange between EDR software and its management console, effectively muting alerts and interrupting the flow of telemetry.
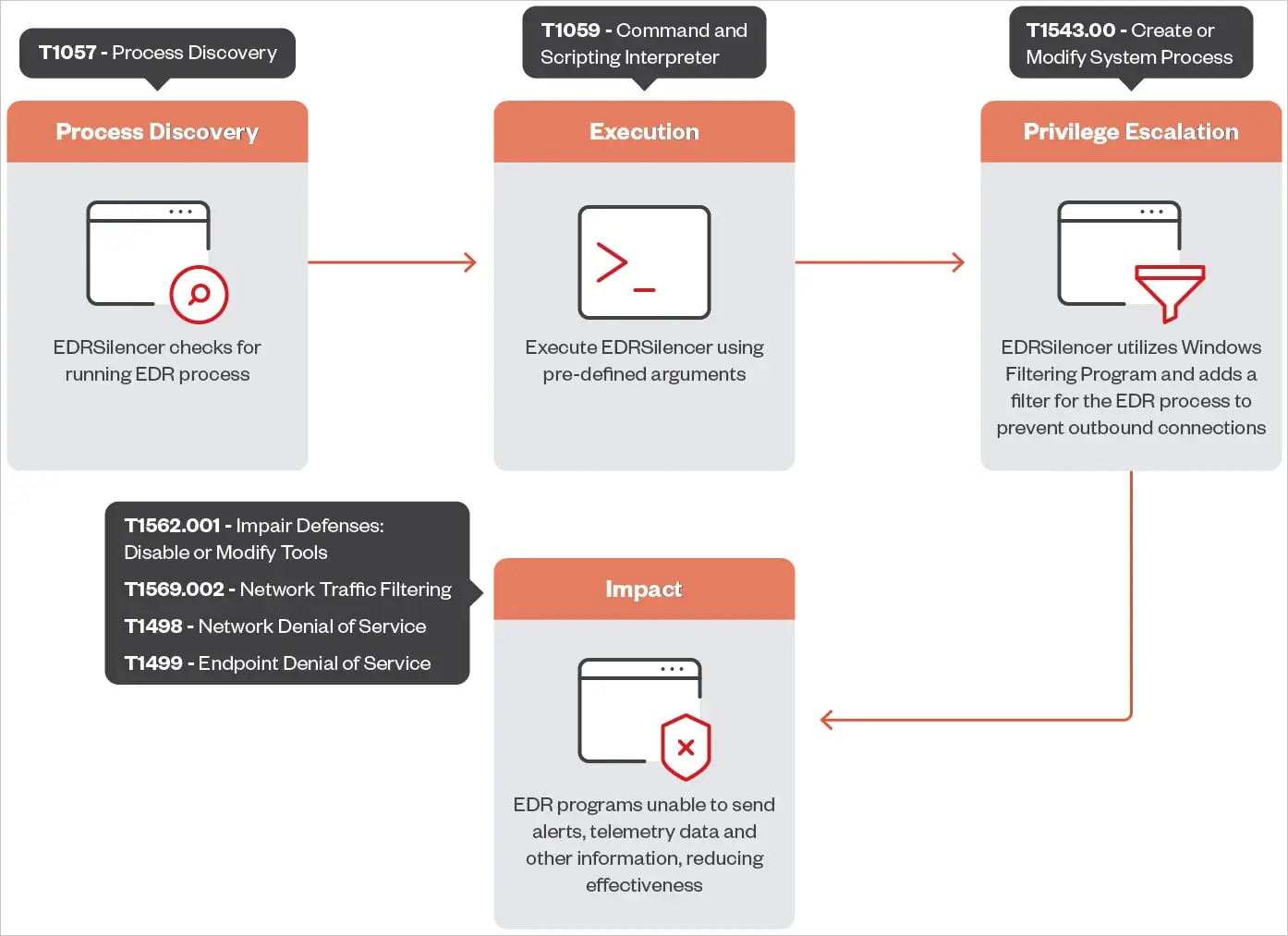
Targeting Leading EDR Tools
In its latest release, EDRSilencer can detect and suppress alerts from 16 widely used EDR solutions, including:
- Microsoft Defender
- SentinelOne
- FortiEDR
- Palo Alto Networks Traps/Cortex XDR
- Cisco Secure Endpoint (formerly AMP)
- ElasticEDR
- Carbon Black EDR
- TrendMicro Apex One
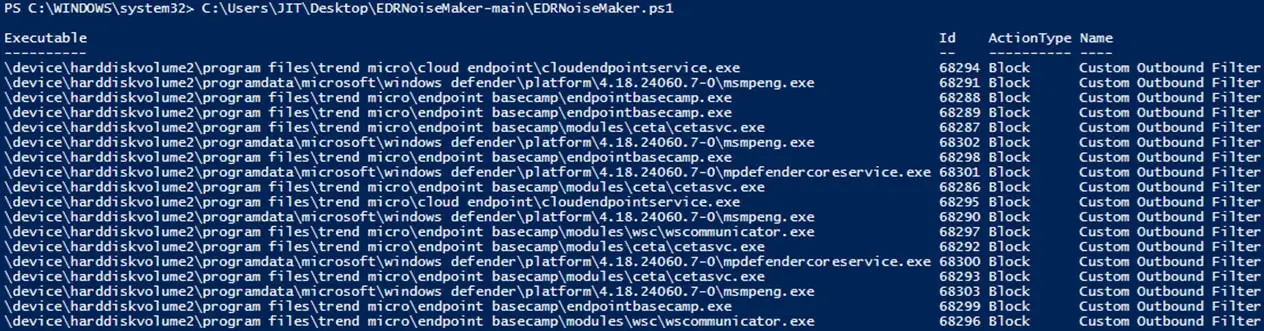
Trend Micro's research indicates that, despite EDRSilencer's capabilities, some EDR tools might still be able to communicate with their management consoles because not all of their processes are part of the tool's default blocking list. However, EDRSilencer offers the flexibility to add custom filters by specifying file paths, allowing attackers to extend the reach of the tool.
“After identifying and blocking additional processes not included in the hardcoded list, the EDR tools failed to send logs, confirming the tool’s effectiveness,” says Trend Micro.
This capability poses a significant risk, as it allows malicious activities to continue undetected, making it easier for attackers to execute successful breaches without alerting security teams.
Trend Micro’s Countermeasures and Recommendations
In response to this rising threat, Trend Micro has developed solutions to identify and flag EDRSilencer as malware, thus intercepting attempts to disable security measures. However, the company emphasizes that mitigating risks from such tools requires a robust and comprehensive security strategy.
Here are some key recommendations from Trend Micro to counter EDRSilencer and similar threats:
Deploy Multi-Layered Security Controls: Use a combination of different security measures to protect critical systems, creating redundancy that makes it harder for attackers to bypass defenses.
Implement Behavioral Analysis and Anomaly Detection: Rely on security solutions that monitor unusual behavior patterns instead of only known indicators of compromise.
Monitor for Indicators of Compromise (IoCs): Regularly scan the network for any signs of potential threats, including unexpected changes in EDR performance or connectivity.
Apply the Principle of Least Privilege: Ensure that systems and users only have the permissions they need, limiting the potential impact of any breach.
The Future of EDR Security
The development and use of tools like EDRSilencer signal a shift in the cyber threat landscape, where attackers are increasingly focusing on disabling defenses before launching more sophisticated attacks. By targeting EDR solutions directly, they aim to eliminate the initial detection phase, giving them more time to execute malicious activities.
Cybersecurity experts stress that the battle between attackers and defenders is constantly evolving, and organizations must remain vigilant. The use of open-source tools, often originating in legitimate penetration testing contexts, highlights the dual-edged nature of cybersecurity technology. As EDRSilencer shows, what begins as a tool for ethical hackers can quickly become a weapon in the hands of adversaries.
Maintaining a proactive defense posture and investing in advanced threat detection systems are crucial steps to ensuring security teams are one step ahead of emerging threats like EDRSilencer. Organizations must also keep up-to-date with the latest intelligence on evolving cyber threats to stay resilient in the face of an ever-changing adversarial landscape.
Read original post here.




