
Germany and Spain Under Siege: Strela Stealer’s Deadly Evolution
In a chilling escalation of cybercrime, employees in Germany and Spain have become the prime targets of a sinister new campaign deploying the notorious Strela Stealer malware. Once a rudimentary credential-stealing tool, the evolved Strela Stealer now stands as a testament to the growing sophistication of cyber threats.
The Campaign Unveiled
Cyble researchers have uncovered this malicious operation, revealing a stealthy and advanced delivery mechanism aimed at compromising mail credentials. The malware’s new iteration demonstrates a significant leap in its ability to bypass conventional security defenses, making it an alarming threat not only to Central and Southwestern Europe but potentially to users worldwide.
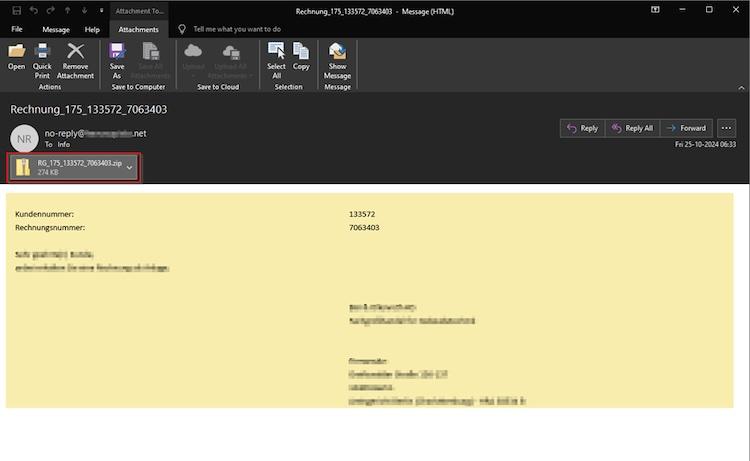
The attack begins innocently enough—with phishing emails disguised as legitimate business correspondence. One German-language example mimics an invoice, luring users to open a ZIP file attachment. Hidden within is an obfuscated JavaScript file that initiates a chain reaction of malicious activity.
This script leverages PowerShell to connect to a WebDAV server, exploiting its collaborative file-sharing features to execute a dynamically modified payload—a DLL file. But here’s the kicker: this DLL file is never saved to disk, making it a ghost in the system and nearly undetectable by traditional antivirus solutions.
The Evolved Strela Stealer
Once activated, the final payload, Strela Stealer, reveals its true capabilities. Since its discovery in 2022, the malware has undergone a remarkable transformation. It now:
Uses control flow obfuscation to render its code analysis nearly impossible.
Avoids disk-based persistence entirely, leaving no traceable footprints.
Employs advanced encryption to safeguard stolen data during transmission.
Executes stealthy data exfiltration while misleading victims with fake error messages.
The malware targets German, Spanish, and Basque users, gathering credentials from email clients like Outlook and Thunderbird, along with system data. It then funnels this sensitive information to an attacker-controlled command-and-control (C2) server, enabling further exploitation.
The Technical Nightmare
What makes this campaign particularly troubling is the complexity of the malicious DLL loader. Packed with conditional jump instructions, it’s designed to crash debugging tools and frustrate even the most skilled malware analysts. Cyble researchers noted that several functionalities fail under default debugger settings, adding another layer of obfuscation to the attack.
A Call to Action
As the Strela Stealer campaign demonstrates, cybercriminals are becoming increasingly adept at evading defenses. The implications are dire: unprotected businesses and individuals face significant risks, from credential theft to potential financial ruin.
Cyble experts stress the urgent need for proactive measures:
Educate employees to recognize phishing attempts and suspicious email attachments.
Deploy robust endpoint protection solutions to detect and prevent advanced threats.
Limit the use of PowerShell and other scripting tools unless strictly necessary.
Enforce strict access controls on WebDAV servers and monitor their usage vigilantly.
A Wake-Up Call for Europe and Beyond
The evolution of Strela Stealer is not just a regional concern—it’s a harbinger of the increasingly sophisticated tactics employed by cybercriminals. Germany and Spain are the latest victims, but this is a stark reminder that no region is immune.
As we face this new age of cyber threats, businesses, governments, and individuals must work together to strengthen defenses. The fight against Strela Stealer and its ilk is far from over.
Read original article here




